Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');]
This is either done by web solutions exposed by each solution or by making it possible for logs to be understandable by all of them. These remedies should have the ability to grow in tandem with the company and also with each other. Misplacing the most up to date safety patches as well as updates is very easy with several safety and security remedies, applications, systems, and tools included.
The more important the source being safeguarded, the extra constant the update cycle requires to be. Update strategies have to be component of the first cybersecurity plan. Cloud infrastructure and also active approach of working make sure a constant development cycle. This indicates brand-new resources and applications are contributed to the system each day.
The 3-Minute Rule for Cyber Security Consulting
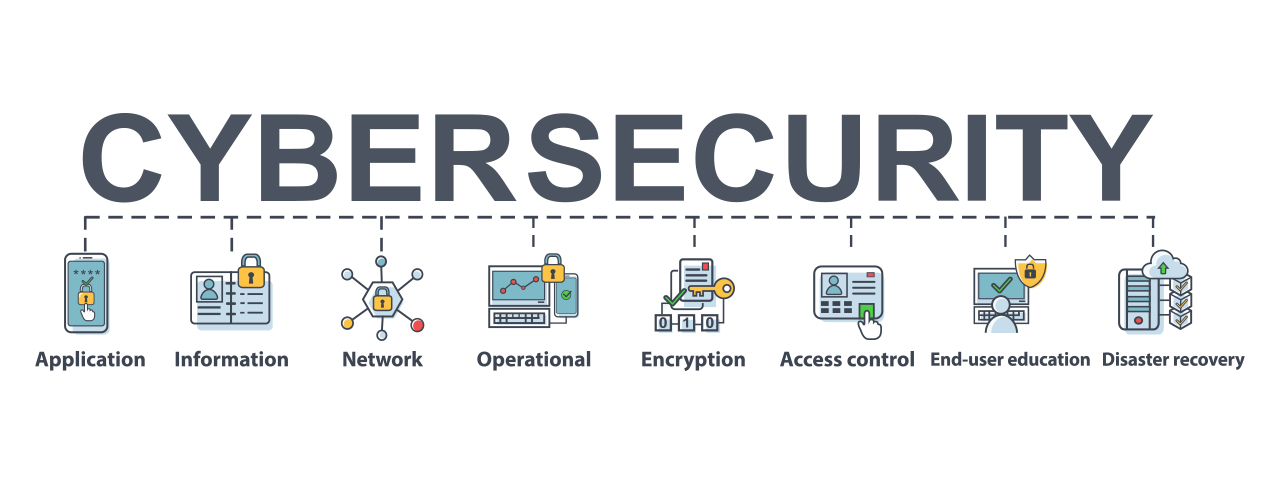
An enlightened employee base has a tendency to enhance protection pose at every level. It appears that no matter the sector or dimension of a company, cybersecurity is an advancing, vital, and also non-negotiable procedure that grows with any type of business. To make certain that cybersecurity efforts are heading in the appropriate instructions, most nations have controling bodies (National Cyber Safety Centre for the U.K., NIST for the united state, and so on), which provide cybersecurity guidelines.
Some Ideas on Cyber Security Consulting You Need To Know
They must be well-informed leaders that prioritize cybersecurity and also directly show their commitment. Numerous directors understand this, however still look for responses on exactly how to proceed. We conducted a study to much better comprehend just how boards deal with cybersecurity. We asked supervisors just how usually cybersecurity was talked about by the board as well as located that only 68% of respondents said frequently or regularly.
When it pertains to understanding the board's duty, there were numerous options. While 50% of participants stated there had been discussion of the board's duty, there was no agreement regarding what that function Check Out Your URL ought to be. Giving guidance to operating supervisors or C-level leaders was seen as the board's role by 41% of participants, joining a tabletop workout (TTX) was stated by 14% of the participants, as well as general recognition or "standing by to react ought to the board be required" was discussed by 23% of Directors.
The Best Strategy To Use For Cyber Security Consulting
It's the figure's function to make certain the organization has a plan and is as prepared as it can be. It's not the board's obligation to compose the plan. There are several frameworks readily available to aid a company with their cybersecurity technique. We like the NIST Cybersecurity go to this website Framework, which is a structure established by the U.S
It is simple and gives execs and directors an excellent structure for analyzing the important aspects of cybersecurity. Yet it additionally has lots of levels of information that cyber experts can utilize to mount controls, procedures, and also treatments. Efficient implementation of NIST can prepare an organization for a cyberattack, and also alleviate the negative after-effects when an assault happens.
The 5-Second Trick For Cyber Security Consulting
While the board often tends to plan about means to take care of service dangers, cybersecurity professionals concentrate their efforts at the technological, organizational, as well as functional levels. The languages made use of to manage business and take care of cybersecurity are different, as well as this might cover both the understanding of the actual threat and the very best method to attend to the basics danger.